Let’s continue our small review of network attacks, by checking this time some typical attacks on the network layer. There are the most known examples of what can be done.
Continue reading
Category Archives: Network
Introduction to network attacks : Physical Layer
That will be a short article, mainly because of two things. First, some methods are beyond my knowledge, involving electronics or hardware manipulation. Second, such methods are not efficient compare to higher level ones, and so rarely used.
The mere concept of a physical attack implies that you have a direct physical access to your target, giving you the ability to modify it as you wish.
This is an ideal situation for an attacker, not quite common. And in that case, there is nothing much to be done on the defensive side.
Practicing Cisco networking with GNS3 and Dynamips
GNS3 and Dynamips put together give a nice open-source and free alternative to emulate a network with IOS routers. Dynampis is an emulator of Cisco 7200 router, while GNS3 provides a nice graphical environment to design your network and use the virtual routers.
I sometimes use Boson Netsim, which is not only non-free but not so reliable.
However, as I just started to use GNS3 and Dynamips, I don’t know it so well yet and won’t compare any further the two solutions.
On this page, I am just summarizing the few steps to set it up on your Linux system.
First, set up the prerequisite :
$ aptitude install python-qt4
Now, go to gns3.net and download the source code for Linux (direct link).
You may extract the archive in your local application folder :
$ wget http://pfe.epitech.net/frs/download.php/819/GNS3-0.5-src.tar.gz $ tar -xzvf GNS3-0.5-src.tar.gz -C /opt
Then, you need the dynamips binary from the dynamips blog (direct links for x86 or amd64 platforms).
The file must be executable.
$ wget http://www.ipflow.utc.fr/dynamips/dynamips-0.2.8-RC2-amd64.bin $ chmod u+x dynamips*.bin $ mv dynamips-0.2.8-RC2-amd64.bin /opt
Now, start GNS3 :
$ /opt/GNS3-0.5-src/gns3
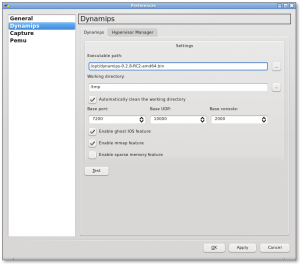
In the edit menu, select preferences and go the dynamips section.
Just browse to the dynamips binary you dowloaded, to fill the value of the executable path field.
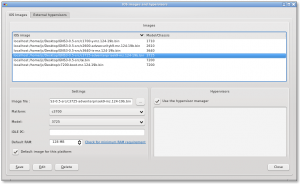
Still from the edit menu, select IOS images and hypervisors. There, you have to add all the IOS images you want to use, one after another. Normally, the default settings for each file loaded are suitable.
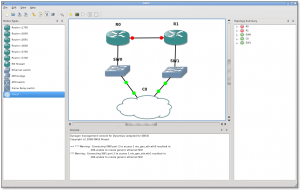
Back to the main window, you can drag and drop routers and link them, creating the topology you wish.
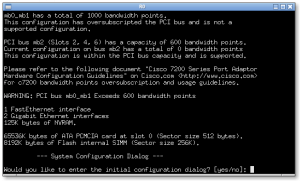
For now, just add one router. Right click on it and select start to start it up. Right click again and select console.
Enjoy ! Of course, I strongly recommand that you start reading further from this page.
Resources :
http://www.ipflow.utc.fr/blog/
http://www.gns3.net/
http://www.blindhog.net/tutorials/gns3-linux-install/gns3-linux-install.html
About network attacks…
I will post later a few examples of network attacks. But, before that, I want to clarify what I call a network attack.
I see many people making a confusion about the use of this term, even among professional or specialized journalists. Whenever there is a hack originated from the Internet, they call it a network attack.
This is a true misunderstanding of the reality. We will see why when a website is hacked, or a domain name spoofed, we can’t call it a network attack.
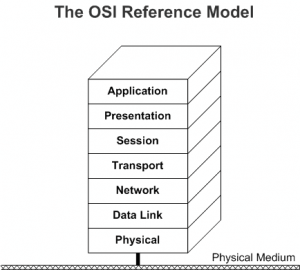
First of all, we need to have a good picture of the way the protocols of the Internet are organized.
We can visualize it with the OSI concept, whose scheme is below :
This model offers 7 layers to contain all protocols involved in the data transportation, from the system or the program of a local computer to its peer on the other side of the network.
FTP configuration issues
I found that it was a real mess to set up a FTP server in a DMZ, behind a firewall Cisco Asa (501 model with IOS version 7.0).
The FTP server is on the DMZ area, and therefore I natted a public IP to the private IP in the DMZ subnet of this server.
static (dmz,outside) <public IP> <private_IP> netmask 255.255.255.255
Doing so, I expect that my FTP server (like Vsftpd on Linux) to be reachable within its public IP, from the Asa external interface.
Continue reading
Perl : how to monitor a service remotely using sockets
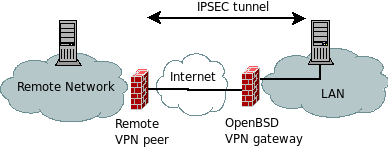
I came to program my first Perl script based on sockets, after setting an IPSEC tunnel.
This tunnel is linking the remote peer and the local peer through an OpenBSD VPN gateway (managed with Isakmp).
The problem is that time allowed for this connection is limited, for security policy reasons. So it is not a 24- hour standard tunnel, but rather an on-demand type connection.
Note that the connection is automatically reset by the remote peer, by invalidating the connection cookie and therefore oblige to renegotiate the VPN tunnel from the beginning (phase 1 of the key exchange).
In other words, the Isakmp service has to be restarted every time we need the tunnel to be up.
Of course, it is not the purpose of Isakmp to have such a mechanism and what we want is to start the tunnel from the local peer, every time it needs to do some transfer.
The graph below summarizes the situation :
That is why I came to develop a script that opens a socket and allows the peer to remotely restart the Isakmp service.