I will post later a few examples of network attacks. But, before that, I want to clarify what I call a network attack.
I see many people making a confusion about the use of this term, even among professional or specialized journalists. Whenever there is a hack originated from the Internet, they call it a network attack.
This is a true misunderstanding of the reality. We will see why when a website is hacked, or a domain name spoofed, we can’t call it a network attack.
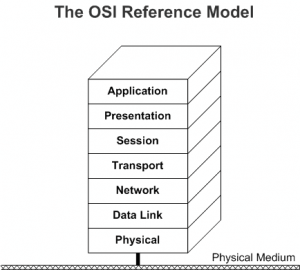
First of all, we need to have a good picture of the way the protocols of the Internet are organized.
We can visualize it with the OSI concept, whose scheme is below :
This model offers 7 layers to contain all protocols involved in the data transportation, from the system or the program of a local computer to its peer on the other side of the network.