I will post later a few examples of network attacks. But, before that, I want to clarify what I call a network attack.
I see many people making a confusion about the use of this term, even among professional or specialized journalists. Whenever there is a hack originated from the Internet, they call it a network attack.
This is a true misunderstanding of the reality. We will see why when a website is hacked, or a domain name spoofed, we can’t call it a network attack.
First of all, we need to have a good picture of the way the protocols of the Internet are organized.
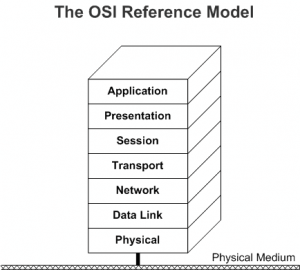
We can visualize it with the OSI concept, whose scheme is below :
This model offers 7 layers to contain all protocols involved in the data transportation, from the system or the program of a local computer to its peer on the other side of the network.
Actually, and to the contrary of another common belief, this model was never really applied on the Internet. Instead, a simplified model of 4 layers was chosen, the TCP/IP model.
Anyway, acconding to this model, each data is encapsulated by the protocols of each layer from the top to the bottom before traveling on the network.
Normally, equipments between the sender and the recipient will not check the data upper than the transport layer. It means that to connect two peers through the Internet, protocols like Ethernet, ARP, RIP, OSPF, IP, TCP and UDP are used.
Protocols like HTTP, DNS, FTP and so many others belong to the Application layer. Therefore, they are used to serve application, not to connect two peers from the network point of view.
Therefore, when a web server is attacked from the Internet, it is not a network attack. It is an application level attack : the network is just a vector, but the vulnerability is at the application level. It may concern the architecture or the conception of the application, but not the network.
So many popular attacks like brute force attacks to guess a password, exploits, shellcodes, DNS spoofing, PHP misconceptions, etc., are off the network attack categories.
Nowadays, as there are more and more services offered on the Internet, application attacks became the most popular and most efficient for attackers. However, if network attacks have been spectacular in the 90s and entered the history, they are still efficient.
Among network attacks, we can differentiate two main categories : protocol vulnerabilities and implementation weaknesses. Of course, it is not that simple and some attacks are a combination of these categories.
Protocol weaknesses
Most of the protocols we use today were conceived in the 80s, or even before. At the name, the engineers never predicted such a growth of the Internet. They did not put much thinking on problems like scalability or security : their needs were very simple and basics, and Internet was very confidential, mostly connecting a few universities in the world.
The growth of the Internet have been so fast, that the protocols could not be adapted at the right pace to the new needs. Now, we inherit of conceptual security leaks at all OSI layers and there is nothing much being done against that.
Implementation weaknesses
The RFC put the bases to implement the protocol in the hardware or in the systems. It implies programming and therefore a classical development cycle : putting down the needs, interpreting the specifications, making arbitrary choices and finally coding. Of course, at any of these stages, there is a potential risk of human mistake, misconception, bug, buffer overflow, unexpected behaviour, etc. Some can be very critical for the whole security of the hardware or the system.
In that case, it is just like an application level vulnerability, but on the IP stack or the drivers handling the network packets. That leads to a network attack.
There is a huge number of vulnerabilities. All operating systems are concerned, as well as all hardware equipments (switches, routers, firewalls, etc.).
That’s it about this short introduction to network attacks. It does not aim to be complete, but just to put the basics of my next articles.
In the coming articles, we will see a few example of network attacks. In the next one, we will start from the bottom of the OSI model : physical layer attacks.