That will be a short article, mainly because of two things. First, some methods are beyond my knowledge, involving electronics or hardware manipulation. Second, such methods are not efficient compare to higher level ones, and so rarely used.
The mere concept of a physical attack implies that you have a direct physical access to your target, giving you the ability to modify it as you wish.
This is an ideal situation for an attacker, not quite common. And in that case, there is nothing much to be done on the defensive side.
It is one of the reason why, as a computer security enginneer, a lot of attention must be always payed on the physical security : access to the machine in a locked room, identification of the persons entering with an electronic card, etc.
Without it, the best security software setting is useless.
There can be many way to implement a physical layer attack : modifying the firmware of a router at the maker itself, plug an electronic sniffer on a network segment, inserting a hub, etc.
Attacks on wireless networks are the most popular and easy to do, because of the nature itself of wifi.
Check at the man of aircrack-ng or one of the numerous wifi craking tutorial on the Net if by any chance you were not aware of it.
Another kind of attacks, that can be done without interfering directly with the hardware, concern the MAC address manipulation.
The MAC address is the “physical” way to identify a machine on the network. This address, supposedly unique world-wide, is set by the network card maker.
It is coded with 48 bits, generally on a read-only chip (ROM) to ensure that it can’t be modified. In reality, all operating systems allow to override this value at a logical level (as seen by the network stack of the system).
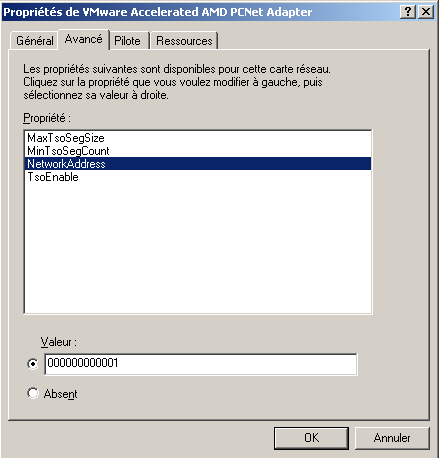
On Windows XP, changing the MAC address of a network card is as easy as going in the advanced properties of the network card driver, changing the value and deactivating / reactivating the network card.
In case it does not work (it depends on the driver), there is a free specific tool : Macshift.
On GNU/Linux, it is even easier. Just fire up these two commands :
$ ifconfig eth1 down hw ether 00:00:00:00:00:01
$ ifconfig eth1 up
As you can see, the MAC address really cannot be considered as reliable way of identification.
At last, the MAC duplicating attack consists in using on the hostile node the same MAC address as an active machine of the same network.
A basic or unprotected switch will see the same MAC address coming from two different ports and transfer the packets to both.