First, thanks for all the comments in the previous articles (Part I and Part II).
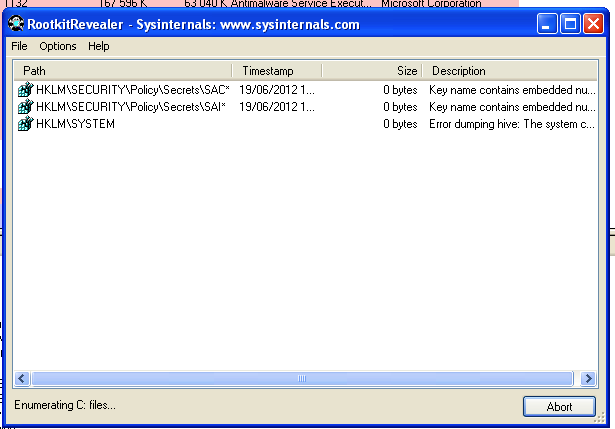
I decided to analyze one the crash I experienced during registry analysis.
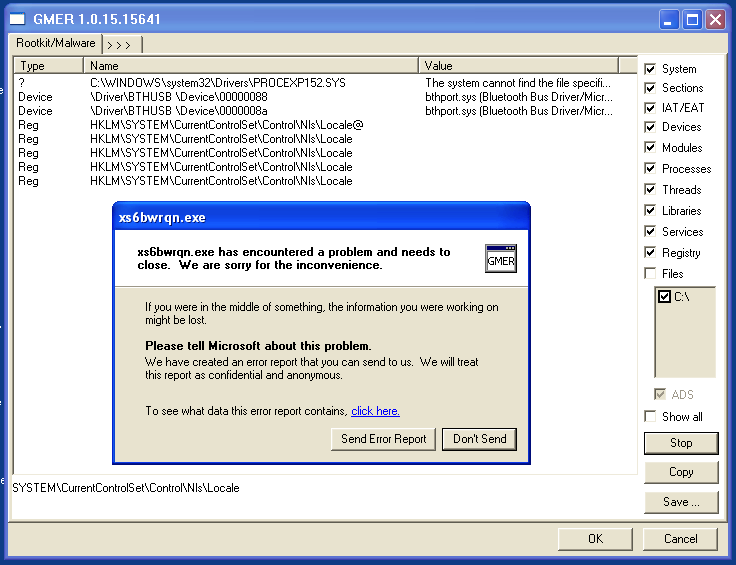
I could reproduce all the time a BSOD with Regshot. I thought it would be nice to see what I could get with WinDBG.
I had my environment set up with the suspicious VM configured to debug activated on the serial port, which is a simple pipe on Mac OS X.
Another VM is configured with a serial port as the other end of this pipe, and WinDBG attached to it.
Another method would be to just configure Windows to create a crashdump file with kernel symbols, that you can later load into WinDBG. Of course, the first method offers more opportunities to check and play with the live system.
Then, I just boot the target and trigger the crash, simply by starting a scan with Regshot:
Windows then crashes, WinDBG catches the exception and stops.
So what do we have ?
First, the error type, PAGE_FAULT_IN_NONPAGED_AREA (50), means that an instruction pointed to an invalid memory address. Let’s check this.
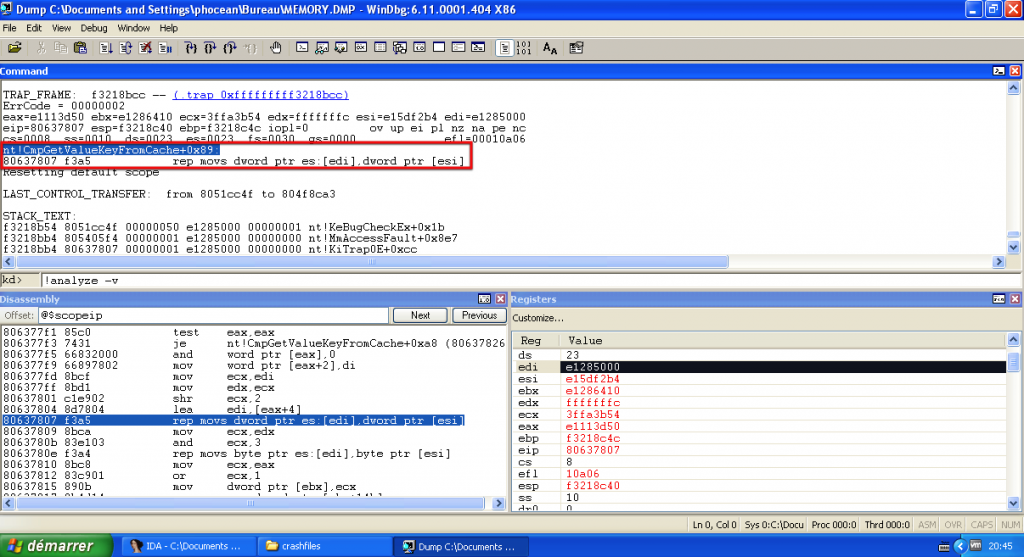
With !analyse -v, you get the full error dump.
It shows the function (nt!CmpGetValueKeyFromCache, offset 0x89) and the memory address where the crash was triggered.
The instruction at this address is:
80637807 f3a5 rep movs dword ptr es:[edi],dword ptr [esi]
This instruction is trying to copy 8 bytes at the address pointed by EDI.
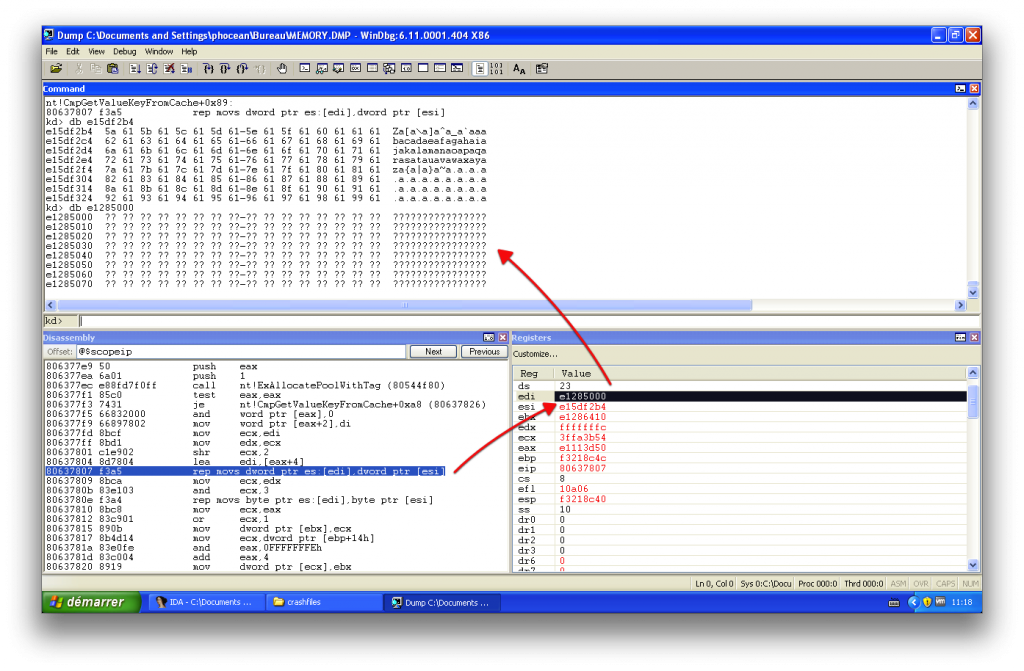
EDI has the value of 0xe1285050 at execution time.
And what do we have at this memory location ?
Nothing indeed. Note that this corruption persists at every boot.
So what can we conclude?
We can certainly exclude hardware failure, because it is a virtual machine and because the corruption always occur at the same memory region, even after a reboot.
At least, I can now be sure that something in the kernel is definitely corrupted.
Could it be a rootkit trick? Still the question remains, but to me it now looks very, very suspicious. Some rootkit code, poorly written, could have sat in this non-paged memory area and been paged out, causing the BSOD. I have not much knowledge about it at this time but I am going to search on this. At least, I now have good starting point to look at.
That’s all for today, folks. I wrote it while I am still working on it, so sorry if it looks rough and incomplete. It is sort of live, thoughts are still in process.
Again, I am looking forward to reading your comments and suggestions. (Hopefully) there will be a part IV!