Mainframes are not dead, why not pentesting it?
I just watched the presentation of Phil Young at Shmoocon 2013: “Mainframed: the secrets inside that black box“. I truly loved it. I thought mainframes where disappearing, but I was surprised to see that it still alive. I was even more surprised to find out that they have some Unix interface, and that there is a emulator for x86. Where it was less of a surprise is that their security is pretty low :-)
Anyway, don’t miss watching the video. Phil’s blog, “Soldier of Fortran”, is also a gold mine, he wrote many tips, tutos and tools.
It made me very curious and just in case I find some IBM Z/OS during a pentest, I though it would be nice to run it.
Installing
Disclaimer:
Although some Z/OS files are available for download on the Internet, you must own a legal license of Z/OS. This tutorial is exclusively for education-purpose, use it only for testing, never in production nor for illegal activities.
Also, I am a noob in the area. So if some of you are skilled and find mistakes or improvements, please let me know in the comments. I give a great importance to your feedback and it encourages me to continue.
I glued the pieces in the following steps (Mac OS oriented and tested only with it, the same should work for Linux with minor adjustments and see the reference otherwise):
- Download and install tn3270 (Mac) or x3270 (Windows, Linux, Mac): this will be the client terminal used to connect to the mainframe.
- Download the emulator, Hercules. Install it, following the README instructions relevant to your system. Note that the instructions for Mac OS are outdated and won’t work. I followed Phil’s instructions:
git clone git://github.com/s390guy/hercules-390.git cd hercules-390 sh autogen.sh ./configure make make install
- Take some IBM Z/OS release, and install it:
mv IBM\ ZOS\ 1.10/Z110SA/images/Z110\ -\ Copy /YOUR/PATH/HERE/Z110
cd /YOUR/PATH/HERE/Z110
mkdir PRTR
cd CONF
cp ADCD_LINUX.CONF ADCD_MAC.CONF
sed -i '' 's/\/home\/ehrocha\/hercules\/images/\/YOUR\/PATH\/HERE/g' ADCD_MAC.CONF
sed -i '' 's/CNSLPORT \{2\}23/CNSLPORT 3270/g' ADCD_MAC.CONF
sed -i '' 's/0E20.2 LCS 10.0.1.20/0E20.2 3088 CTCI \/dev\/tun0 1500 10.10.10.11 10.10.10.12 255.255.255.255/g' ADCD_MAC.CONF
- Getting the network to work on Mac OS require some extra steps (skip it if your are using Linux).
Download tuntaposx, uncompress and install the package. No reboot it necessary, you should now have plenty of tun* (and tap*) interfaces:
$ ls /dev/tun* /dev/tun0 /dev/tun10 /dev/tun12 /dev/tun14 /dev/tun2 /dev/tun4 /dev/tun6 /dev/tun8 /dev/tun1 /dev/tun11 /dev/tun13 /dev/tun15 /dev/tun3 /dev/tun5 /dev/tun7 /dev/tun9
- Okay, now we can start the emulator (we need to sudo to access to the tun0 interface, among other reasons):
sudo hercules -f ADCD_MAC.CONF
First of all, checks that the network is fine:
# From Mac OS: $ ifconfig tun0 tun0: flags=8851<UP,POINTOPOINT,RUNNING,SIMPLEX,MULTICAST> mtu 1500 inet 10.10.10.12 --> 10.10.10.11 netmask 0xff000000 open (pid 98687) # From Hercules: herc =====> devlist [...] HHC02279I 0:0E20 3088 CTCI 10.10.10.11/10.10.10.12 (tun0) IO[0] open HHC02279I 0:0E21 3088 CTCI 10.10.10.11/10.10.10.12 (tun0) IO[0] open
Open tn3270 and connect with default settings on localhost:
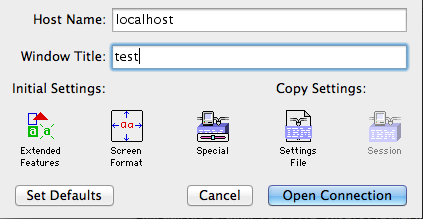
And then in the hercules terminal, enter ipl a80
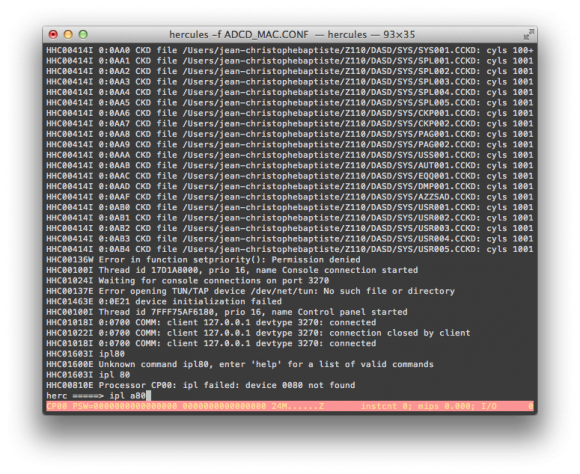
Hercules390 console: booting Z/OS
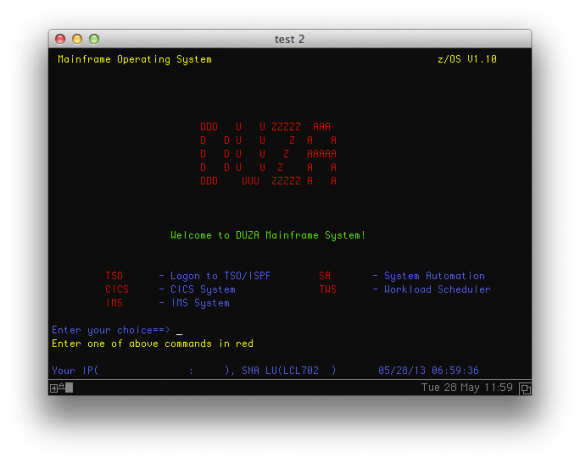
It is very long to boot, don’t worry. You will actually have to use 2 terminals, so open the second one, which will show the logon screen (see screenshot below) after booting is done. It will be used for “userland” aka TSO commands.
The first terminal shall be kept open as the master console, which receive system logs and can be used for “system-level”* commands (e.g root level).
- At the prompt, enter
TSO, thenIBMUSERas the login, andSYS1as the password. It will automatically launch the ISPF menu:
- Now, you are good to go ahead with Z/OS commands…
This video demonstrates the boot process:
Z/OS emulation with Hercules390 from phocean on Vimeo.
- Now, let’s get the network up.
Prepare Mac OS:
- Make sure that the Mac OS firewall is deactivated or/and that you configured pf to allow the
tun0interface (another article coming soon on this topic). - Add a route to
tun0
sudo route add -net 10.10.10.0/24 -interface tun0
- You may want to activate ip forwarding, to have the Z/OS reach other interfaces through the kernel:
sudo sysctl -w net.inet.ip.forwarding=1
Now every thing is in place to allow the mainframe to reach the outside. Further routing considerations are outside the scope of this article.
Prepare Z/OS:
- In TSO menu, choose 3 (utilities), 4 (Dslist)
- Click on the line besides
Dsname Leveland type-inADCDand then press[Enter]. ADCD is what is called a dataset. - In the Command column, on the left of
ADCD.Z110S.PROCLIB, type ine(stands for edit, reproduce the same pattern when I say “edit” in the following steps) - Edit the TCPIP member, and make sure that the
//PROFILEline looks like this:
//PROFILE DD DISP=SHR,DSN=ADCD.Z110S.TCPPARMS(DUZA)
You could change the DUZA string, but you would have to make sure that the corresponding profile exists in ADCD.Z110S.TCPPARMS (see TODO section).
- Go back to
Dslistpage using end or exit as a command. This time, typeDUZAas dataset. - Edit the
TCPARMSmember, thenPROFILE. Once in the file, edit carefuly the following lines (at the bottom, around line 90):
000090 DEVICE CTCA1 CTC e20 000091 LINK CTC1 CTC 1 CTCA1 000092 000093 HOME 000094 10.10.10.11 CTC1 000095 000096 GATEWAY 000097 10.10.10.12 = CTC1 1492 HOST 000098 000099 DEFAULTNET 10.10.10.12 CTC1 1492 0 [...] 000109 START CTCA1
- In the console window, restart the network stack:
stop tcpip # wait for termination message start tcpip
- If every is going well, the tunnel should get up and you should be able to ping both side (use the ping command in Z/OS from the command menu).
This video illustrates some of this networking stuff:
Hercules390 and Z/OS, getting the network up from phocean on Vimeo.
Useful commands
- Ifconfig
netstat home
- Shutdown
# in "system" terminal: S SHUTSYS Z EOD # then, once finished, in Hercules: exit
Tips
- I was stuck at an early moment during the boot process with:
IXC208I THE RESPONSE TO MESSAGE IXC420D IS INCORRECT: IS NOT A VALID ACTION IXC420D REPLY I TO INITIALIZE SYSPLEX ADCDPL, OR R TO REINITIALIZE XCF. REPLYING I WILL IMPACT OTHER ACTIVE SYSTEMS.
You can go over it by entering this in your terminal session (tn3270):
R 00, I
- After the long process, I actually had to open a second connection with the terminal to get the logon screen. So, just check from time to time instead of waiting for nothing in front of the first window.
- To logoff, type
Xfrom the ISPF main menu. The first time, you have to configure the printer. ChooseLOCALas print mode, and give it any name asLocal printer ID. Then press[Enter], and if you are asked for asysout class, choose"J". You should be back in TSO, where you can executelogoff. Next time, it will default to these values, so you should get straight from ISPF to TSO. - Don’t forget that TSO is a CLI where you can type Z/OS and Unix commands. You actually don’t need or have to use ISPF, so don’t hesitate to use it!
Of course, a good source of information is the hercules390 forum may also be of help.
Voilà, happy hacking! WTF, it seems I got mainframed too! Did you?
Big thanks again to Phil Young for catching our attention on this stuff.
TODO
- Understand and get rid off the DUZO profile: you probably noticed that we are using the DUZO profile to load the network stack (which is after the name of the torrent, and does probably more stuff behind). For example, there is no DUZO profile in ADCD.Z110S.TCPPARMS, so I still have no idea how it actually gets loaded. It has been only 2 days that I work on Z/OS, so I still have to read the doc (and any help is welcome).
- Change the logon screen (see references).
References
- Hercules 3.08 on Mac OS X Lion
- Instructions to installing z/OS in Hercules
- Installin’ that sweet sweet big iron on your Linux laptop or server (local mirror)
- Z/OS files
- Hercules and Z/OS TCP/IP networking for ADCD versions
- Changing the logon screen on the mainframe
- tuntaposx
- TSO tutorial
- Mainframe – using TSO and ISPF
- IBM online documentation