I just tested the Mimikatz plugin for Volatility and it worked very well on a Windows 7 dump:
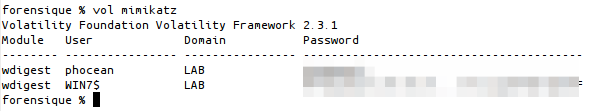
Output of the Mimikatz plugin for Volatility
Good job ;-)
I just tested the Mimikatz plugin for Volatility and it worked very well on a Windows 7 dump:

Output of the Mimikatz plugin for Volatility
Good job ;-)
I finished checking the RAM with Volatility and… I found nothing. Nada.
It’s a lot of fustration. There must be something just there, but my findings are certainly limited by my skills.
I attach here some of the main outputs of Volatility. As far as I can tell:
Based on my observations, I first tried to narrow my investigations (drivers and hooks) but as I could not find anything, I ended dumping most of Volatility outputs in hope to see something unusual. I also compared them with a fresh Windows XP SP3 install. I extracted keyboard related drivers (keyboard.sys, kbdclass.sys, i8042prt.sys), hashed them, scanned them: there were native. I am less sure on how to deal with the software certificate system, but I did checked all Microsoft and root certificates in the bank along with their signature with a clean system: nothing wrong.
Dear reader, any help or tip is welcomed! Am I missing something obvious? Could it be possibly not a rootkit but some kind of corruption? If so, how to detect it?
Just drop me an e-mail if you want to have a look on the dump itself.
Volatility outputs:
For now, I can’t tell much about the context, mainly because it may – or may not – involve other people. The only thing I am interested in is to spot the issue and understand precisely what is going on.
What makes the case really interesting though, is that it occurred on a fresh install of a Windows XP virtual machine. I aimed it to be a clean malware reversing snapshot. I noticed the weired behavior minutes after finishing the system install and setting up a bunch of reversing and live analysis tools.
So I bet that if I got some malware, it probably comes from one of those. At this time, unfortunately, there are too many and I could not spot the exact time, so I can not start the analysis from this angle.
This article is almost written in live, so pardon my mistakes. I will update it as soon as I find something new. Of course, I am really expecting your feedback, suggestions and corrections. I see it as a great opportunity to learn, even though this one may not be the easiest…
Two things alerted me quickly.
The first one was, at a point, the permanent failure of going through the full windows update process. Believe me, I have tried all ways.
The second one was the weird dialog when trying to access to the keyboard layout settings. It says “Incompatible driver detected“. To me, this looks like there is a keylogger somewhere…
Then, as I started to check around, more odd stuff came out.
I fired up Process Explorer, and soon realize that it was “unable to verify” the signatures of all the running Windows processes. I could not find anything else suspicious, though (no odd process, memory content looks normal, etc.).
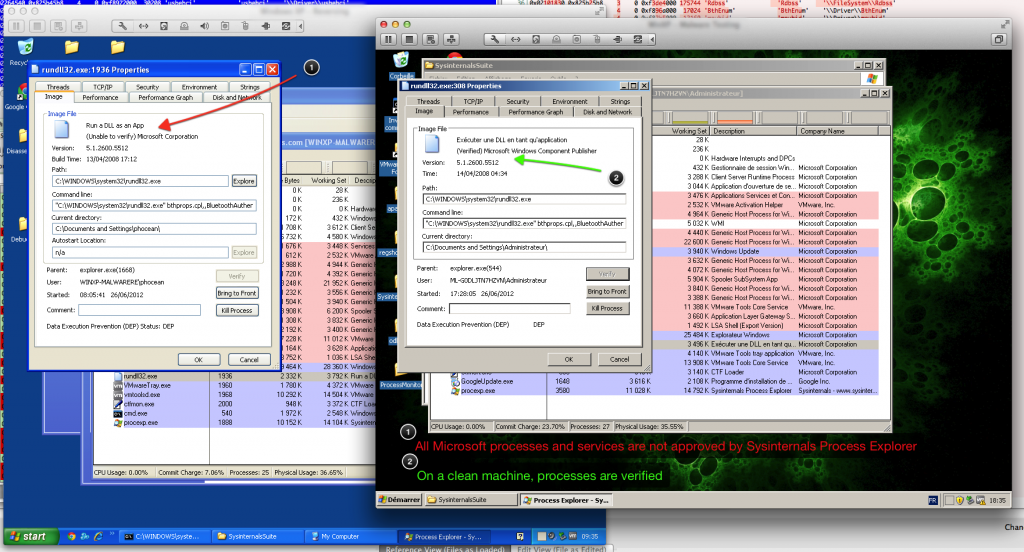
On the left, Process Explorer fails to validate any Windows process.
On the right, expected behavior on a clean system.
Ok, while I am with the Sysinternal suite, why not scanning with Rootkit Revealer:
Interesting… and what about GMER:
Oops! Now it crashes when it is accessing the registry…
For the fun, let’s see what happens if we try to set up an antivirus (Security Essentials):
Nice one! Very suspicious! Note that after a full scan, Security Essentials reports me that the system is clean and everything is fine. I am so relieved. :)
Curious to see how my certificates are, I run certmgr.msc. I compared all Microsoft root certificates with a clean machine and could not see anything different. But again something happened:
Oh, just one of my last attempts to do live analysis (this the WinPcap setup included with Wireshark):
Ok, so enough played. The thing seems to be nicely done, and live analysis is going to be way too hard and unreliable.
This is where I am now. I reverted to a snapshot prior to my live analysis attemps, confirmed the strange behaviors are still observable, and suspended the VM to get the vmem file.
So I have spent the last hours scanning the memory with, of course, Volatility.
So far, I have to confess that I found NOTHING. But analyzing the memory can be a harsh process when it comes to sophisticated threats, and I may have reached the limits of my skills.
But, anyway, I could not dream of a greater and more exciting opportunity to learn!
My discoveries, if there are, will be published in another article.
UPDATE: I forgot to tell that it is a Windows XP SP3 machine, but not fully updated due to the issues.