DecaffeinatID is a tool for Windows that can be very useful against ARP attacks.
Author Archives: phocean
Introduction to network attacks : Physical Layer
That will be a short article, mainly because of two things. First, some methods are beyond my knowledge, involving electronics or hardware manipulation. Second, such methods are not efficient compare to higher level ones, and so rarely used.
The mere concept of a physical attack implies that you have a direct physical access to your target, giving you the ability to modify it as you wish.
This is an ideal situation for an attacker, not quite common. And in that case, there is nothing much to be done on the defensive side.
Practicing Cisco networking with GNS3 and Dynamips
GNS3 and Dynamips put together give a nice open-source and free alternative to emulate a network with IOS routers. Dynampis is an emulator of Cisco 7200 router, while GNS3 provides a nice graphical environment to design your network and use the virtual routers.
I sometimes use Boson Netsim, which is not only non-free but not so reliable.
However, as I just started to use GNS3 and Dynamips, I don’t know it so well yet and won’t compare any further the two solutions.
On this page, I am just summarizing the few steps to set it up on your Linux system.
First, set up the prerequisite :
$ aptitude install python-qt4
Now, go to gns3.net and download the source code for Linux (direct link).
You may extract the archive in your local application folder :
$ wget http://pfe.epitech.net/frs/download.php/819/GNS3-0.5-src.tar.gz $ tar -xzvf GNS3-0.5-src.tar.gz -C /opt
Then, you need the dynamips binary from the dynamips blog (direct links for x86 or amd64 platforms).
The file must be executable.
$ wget http://www.ipflow.utc.fr/dynamips/dynamips-0.2.8-RC2-amd64.bin $ chmod u+x dynamips*.bin $ mv dynamips-0.2.8-RC2-amd64.bin /opt
Now, start GNS3 :
$ /opt/GNS3-0.5-src/gns3
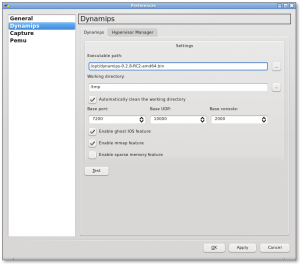
In the edit menu, select preferences and go the dynamips section.
Just browse to the dynamips binary you dowloaded, to fill the value of the executable path field.
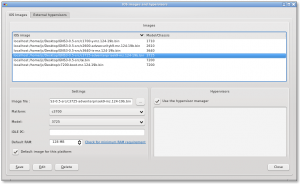
Still from the edit menu, select IOS images and hypervisors. There, you have to add all the IOS images you want to use, one after another. Normally, the default settings for each file loaded are suitable.
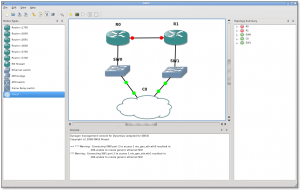
Back to the main window, you can drag and drop routers and link them, creating the topology you wish.
For now, just add one router. Right click on it and select start to start it up. Right click again and select console.
Enjoy ! Of course, I strongly recommand that you start reading further from this page.
Resources :
http://www.ipflow.utc.fr/blog/
http://www.gns3.net/
http://www.blindhog.net/tutorials/gns3-linux-install/gns3-linux-install.html
Ryan Farmer is a spammer
For those who still don’t know, Ryan Farmer would be a spammer and a liar.
Quite embarassing to be caught like that. Maybe all this is a lot of noise, but such people deserve a good lesson of living in society. Really.
Windows Vista memory protection : defeated ?
It seems, at least according to some researchers showed it at the Black Hat conference.
Mark Dowd (IBM) and Alexander Sotirov (VMWare) found a way to bypass the memory protection implemented in Vista to inject malicious instructions within Internet Explorer. They were able to copy any content wherever they wished on the disk.
Especially, this paper will be an interesting reading, even if it is not as simple as they say – at least for me.
How-to : Mod-security 2 set-up for Apache 2
Mod-security is a security proxy for Apache. It adds a frontal layer filtering unwanted clients, malformed packets and malicious requests.
It is especially usefull if your website is dynamic, involving php, sql, javascript, etc. With such a complex environment, as you can never be sure that your website is not vulnerable or up-to-date enough, something like mod-security provides an interesting extra-security layer.
Continue reading