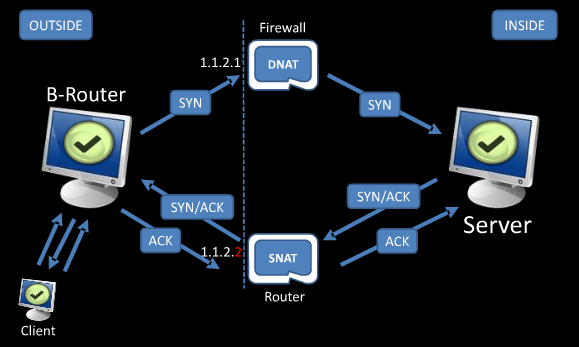
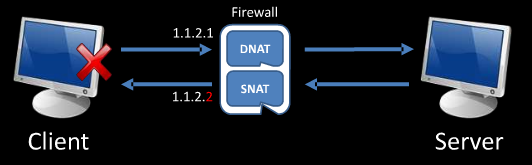
BNAT stands for “Broken NAT“. In the scope of Jonathan Claudius work, a NAT is considered broken when the client receives a reply from a server behind a NAT with a different IP than the one it sent the request to.
It happens with bad implementations where the DNAT (destination NAT) and the SNAT (source NAT) use a different IP because of a wrong rule or because the outbound and inbound interfaces are separated.
As a result, the operating system of the client will discard right away such a reply (with a TCP RST), because it does not match an existing TCP session.
The idea is that a pentester auditing such an infrastructure with a classic scanner will miss some entry points. A typical scanner relies on the network stack of the system : it will not receive the reply and will consider the port as filtered.
So Jonathan came with a proof-of-concept to illustrate his purpose.
It is composed of a B-Router and a client. The B-Router will intercept the reply and maintain the session by sending an ACK. This way, it handles an asymetric routing scheme for the client. Just add a filtering rule to block your system’s RST (iptables -A OUTPUT -p tcp –tcp-flags RST RST -j DROP ), and you are good to go.
Simple but brilliant, isn’t it ? The great thing is that the code has now been included in Metasploit, so it is even more straightforward.
Check the slides of Jonathan at DEFCON for more info. You can download the source there (or just update your Metasploit and look for it in auxiliaries).