Analyzing the MBR is sometimes required during a forensic process, if you suspect a malicious activity that is not detected on-line. With static analysis, you may see if an obvious corruption happened, but you will need to debug to learn more.
Prerequisite :
- IDA Pro (6.0) with the IDA Python plug-in (1.4.3)
Steps :
- Prepare your forensic disk image.
In general, it is that simple :$ dd if=<source> of=disk.img bs=65536 conv=noerror
Or :
$ ddrescue -n <source> <dest> file.log
Check the disk geometry using :
$ fdisk -luc disk.img
These values will be useful for step 5.
However, if you have an exotic disk, it may be much trickier. For example, I got some geometry errors with a flash disk when using Bochs at step 11. Special thanks to Gene Cumm from the bochs-developpers mailing list who gave me the tip to specify the geometry to dd :$ dd if=input of=output bs=2064384 count=507
- Extract the MBR from the disk or from the image you just took.
$ dd if=<source> of=mbr.dump bs=512 count=5
- Download and install the Bochs x86-64 emulator, which comes with a debugger that will work nicely with IDA.
- Download this archive from Hexblog (IDA Pro’s blog). We will use two files from there : bochrc, wich is the configuration file for Bochs, and mbr.py which a python file helpful from preparing the debugging environment.
- Copy bochrc in your working directory and edit the following line to match your disk image geometry :
ata0-master: type=disk, path="sdb.img", mode=flat, cylinders=507, heads=64, spt=63
Before going on, you may test that Bochs can use the image with these settings :
C:\>"c:\Program Files\Bochs-2.4.5\bochsdbg.exe" -f bochsrc -q
- In the same directory, copy mbr.py and edit the following settings :
# Some constants SECTOR_SIZE = 512 BOOT_START = 0x7C00 BOOT_SIZE = 0x7C00 + SECTOR_SIZE * 4 BOOT_END = BOOT_START + BOOT_SIZE SECTOR2 = BOOT_START + SECTOR_SIZE MBRNAME = "mbr.img" IMGNAME = "sdb.img"
- Now open a console and type :
C:\> mbr update
- With IDA Pro, open the boshrc file. IDA should recognize the format and set the proper settings.
- From the menu, open File/Script File and select mbr.py. It will close IDA after execution.
- Open again your *.idb file, set a breakpoint at 0x7C00.
- Start the debugger.
Refer to CHS if you wonder how to get these values.
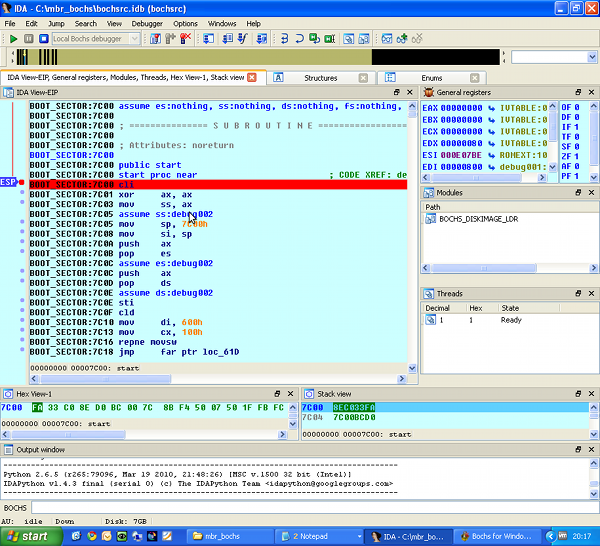
You should now be able to go ahead and debug the MBR step by step.
References :
- Hexblog : Develop your master boot record and debug it with IDA Pro and the Bochs debugger plugin
- MISC Magazine #53 : Votre MBR pris en otage ! – Nicolas Brulez (Kaspersky labs)
- Bochs User Manual : Chapter 8, Tips and Techniques