Soktspy is a small script that may be helpful for some investigation.
Sometimes, you may detect that some suspicious network traffic coming out from a machine. In general, it is easy to spot the process from which the packets originate. You somehow connect to the PC and look for open sockets.
But sometimes, the behavior may be very sneaky, consisting of one or two packets, at rare and random intervals. Unless you spend all the day before the screen, it may be very difficult to trace.
Especially with stock tools or without installing any intrusive hardware, which is also the reason why I did this tool. On a production server, you want to install as little dependencies as possible, right?
So here is the Soktspy, a python script that easily build into a portable and standalone executable to deploy on the target machine.
Once launched, it just loops in the background and log sockets that are created for some given peers (the IP addresses you found involved in the suspicious network activity).
Maybe, some other tool exist, but I could not find anything similar. Let me know if you have any suggestion. Anyway, it was a nice exercise to do :)
Download
Pre-requisites
- Install Visual C++ Runtime libraries with vcredist_x86.exe (not necessary if the target machine happens to have Python already installed)
Compiling
You may recompile the program as a Windows binary executable by issuing this command:
setup.py py2exe
How to use
- Copy soktSpy.exe and its configuration file config.cfg.
- Edit config.cfg with the IP you want to monitor
- Start soktSpy.exe.
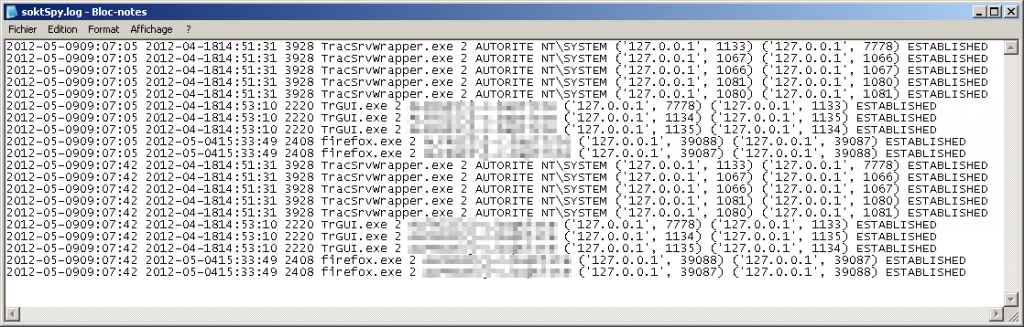
Then, as soon as the sneaky process will send out a packet toward the monitored IP, a log record will be triggered:
The log file contains the following info, in that order:
- Detection time (based on the system local time)
- Process creation time
- PID
- Process Name
- Protocol Family (2 = IPv4, 23 = IPv6)
- Process Owner
- Source socket (IP, port)
- Destination socket (IP, port)
- Socket Status
Future Plans
Please tell me if you have any idea on how to improve it.
For now, I plan to add a feature that will dump the memory of the suspicious processes when it is executing.